A little while ago I wrote a post over on openshift.com about installing Openshift 4 on VMware. Some of you reading it have asked me how I configured the DNS in my particular set up so this post aims to outline that for you.
My current firewall software of choice is opnsense, a fork of the popular pfsense project. Both of these projects share a lot of DNA, including their usage of the DNS server unbound.
Note this post was written to compliment the openshift.com blog post and was tested against OCP 4.3.
Configuring unbound wasn't particularly difficult but it did take a bit more Googling than I'd like to admit. Firstly you should examine the DNS requirements for Openshift 4.
Here's how I laid out the hosts needed for a fairly minimal homelab grade cluster.
| Node | FQDN | IP Address | Other Info |
|---|---|---|---|
| lb | lb.ocp4.ktz.lan | 192.168.1.160 | RHEL7 |
| master1 | master1.ocp4.ktz.lan | 192.168.1.161 | etcd-0.ocp4.ktz.lan |
| master2 | master2.ocp4.ktz.lan | 192.168.1.162 | etcd-1.ocp4.ktz.lan |
| master3 | master3.ocp4.ktz.lan | 192.168.1.163 | etcd-2.ocp4.ktz.lan |
| worker1 | worker1.ocp4.ktz.lan | 192.168.1.164 | |
| worker2 | worker2.ocp4.ktz.lan | 192.168.1.165 | |
| webserver | ignition.ocp4.ktz.lan | 192.168.1.168 | RHEL7 |
| bootstrap | bootstrap.ocp4.ktz.lan | 192.168.1.169 | RHCOS |
Requirements
The following records need to be created and pointed at the load balancer. Do this under Services -> Unbound DNS -> Overrides. Top tip here is to use aliases.
* lb.ocp4.ktz.lan
* api.ocp4.ktz.lan
* api-int.ocp4.ktz.lan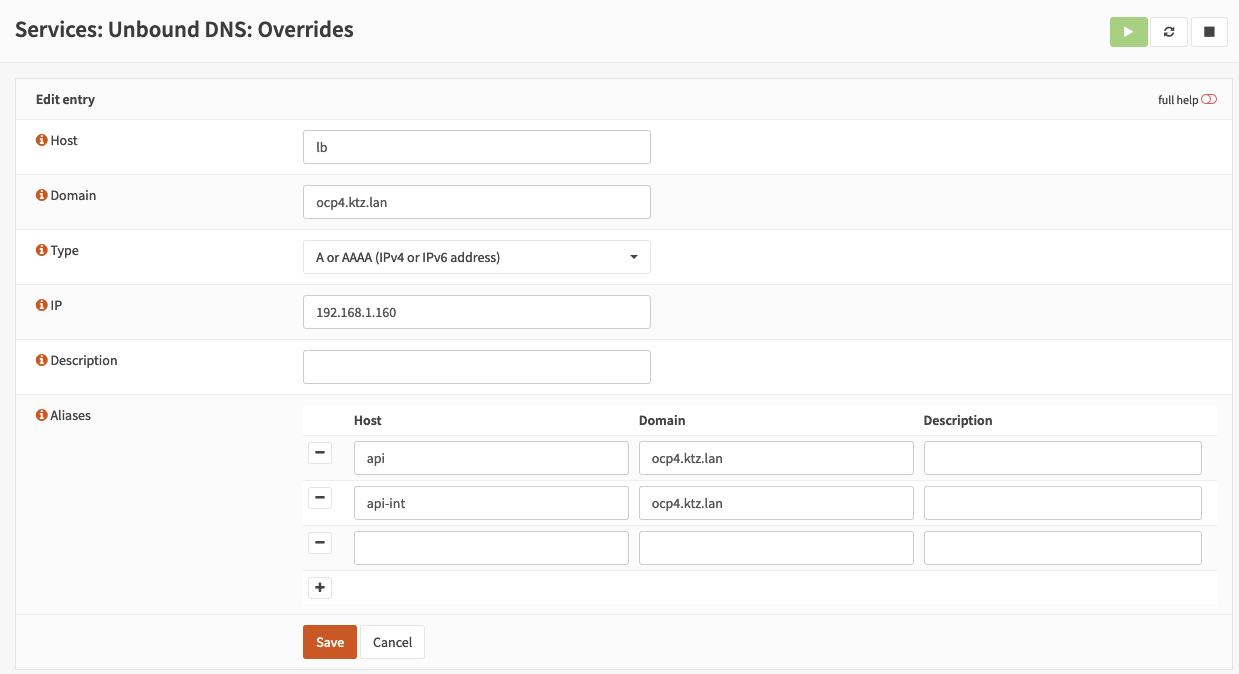
Wildcard records
The apps subdomain needs a wildcard entry. With Unbound on OPNsense you can do this via Services -> Unbound DNS -> General -> Advanced -> Custom Options.:
server:
local-zone: "apps.ocp4.ktz.lan" redirect
local-data: "apps.ocp4.ktz.lan 86400 IN A 192.168.1.160"
Verify with dig:
[alex@ktzTP redhat]$ dig *.apps.ocp4.ktz.lan +short
192.168.1.160
SRV records
OPNsense uses Unbound and to create SRV records use the following code under Services -> Unbound DNS -> General -> Advanced -> Custom Options.
server:
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-0.ocp4.ktz.lan."
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-1.ocp4.ktz.lan."
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-2.ocp4.ktz.lan."
Verify with dig:
[alex@ktzTP redhat]$ dig _etcd-server-ssl._tcp.ocp4.ktz.lan SRV +short
0 10 2380 etcd-0.ocp4.ktz.lan.
0 10 2380 etcd-1.ocp4.ktz.lan.
0 10 2380 etcd-2.ocp4.ktz.lan.
Configuring custom options
Custom options are needed because not everything is configurable via the UI. Using the menu Services -> Unbound DNS -> General and the Custom options box (might be hidden under Advanced on first load).
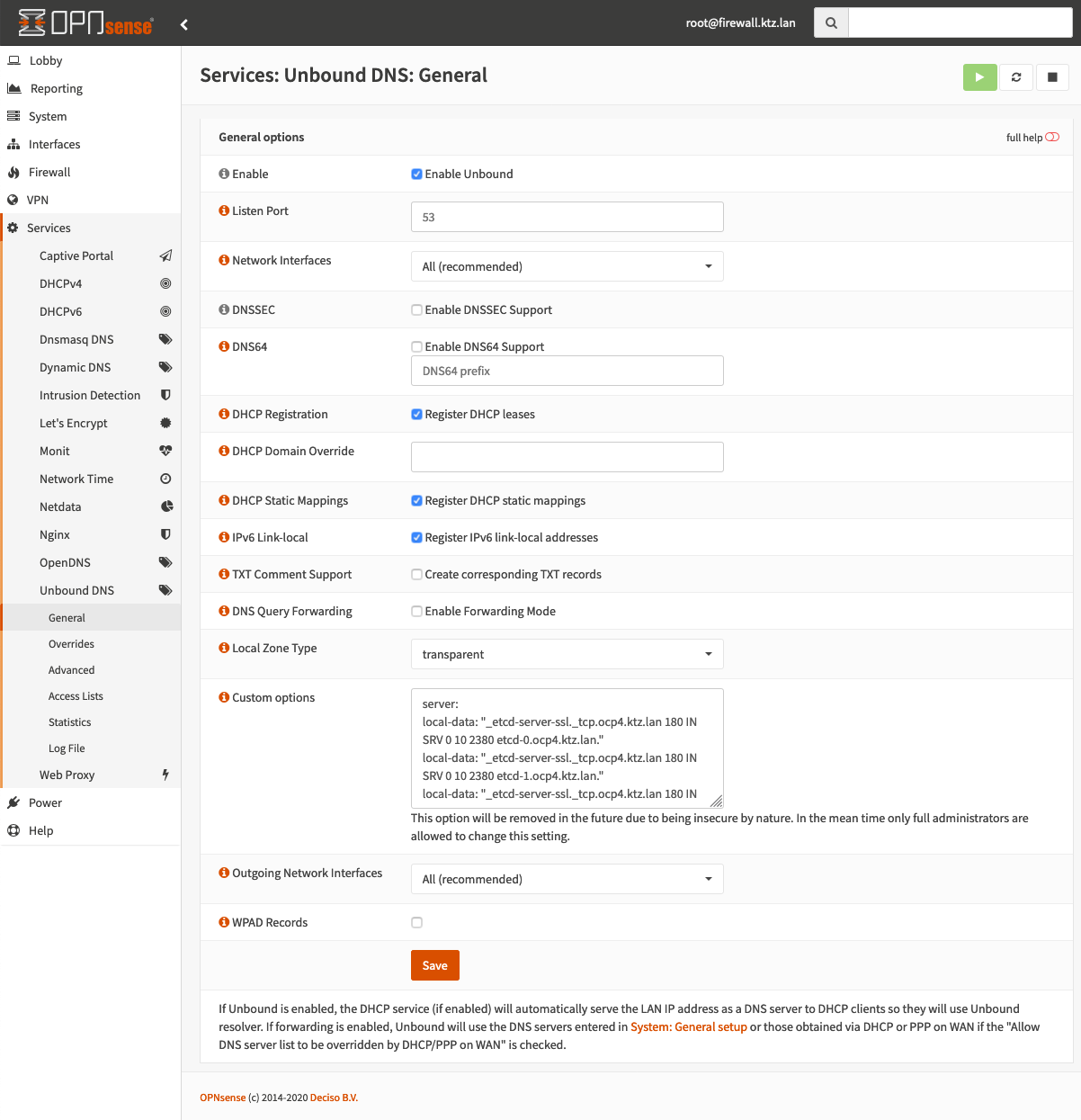
Here, we can configure some required custom options. Namely the SRV, PTR and wildcard records.
server:
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-0.ocp4.ktz.lan."
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-1.ocp4.ktz.lan."
local-data: "_etcd-server-ssl._tcp.ocp4.ktz.lan 180 IN SRV 0 10 2380 etcd-2.ocp4.ktz.lan."
local-zone: "apps.ocp4.ktz.lan" redirect
local-data: "apps.ocp4.ktz.lan 86400 IN A 192.168.1.160"
local-data-ptr: "192.168.1.161 etcd-0.ocp4.ktz.lan"
local-data-ptr: "192.168.1.162 etcd-1.ocp4.ktz.lan"
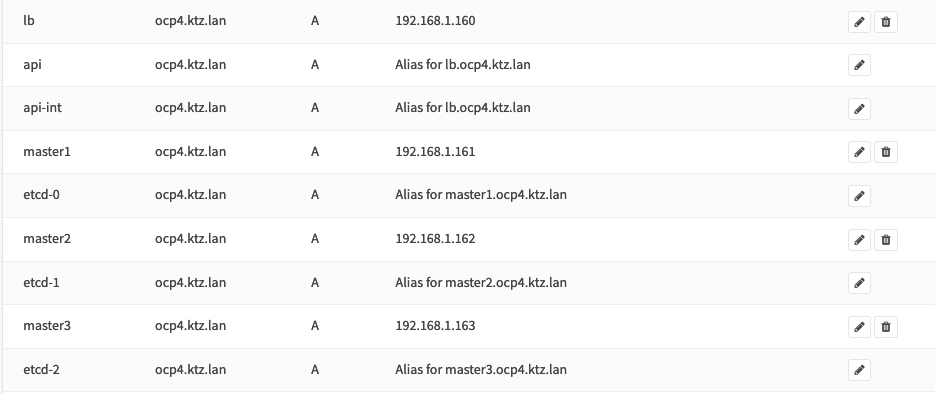
local-data-ptr: "192.168.1.163 etcd-2.ocp4.ktz.lan"Next, we need to configure the overrides for each host. Use the Services -> Unbound DNS -> Overrides menu for this. Here's an overview of some of my entries.
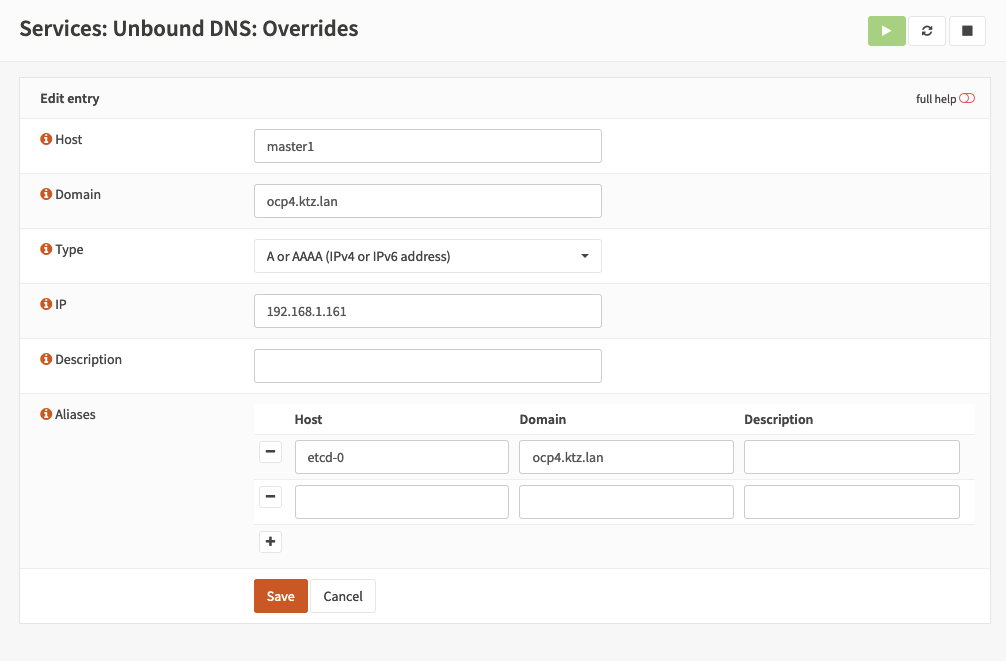
To save configuring the same thing over and over you can make use of aliases so that if your master1 IP changes, etcd-0 will change with it. Like this:
That should be it. Feel free to reach out on to me Twitter, I'm @IronicBadger, with any questions or comments.
For more information on actually installing Openshift 4 you can refer to my original blog post on openshift.com or this github repo, which contains the artifacts required to deploy Openshift using automation.
